Configure SAML SSO for Application
Safous ZTA's SAML SP SSO solution is innovative, allowing users who use Safous ZTA an added layer of protection, a proxy that monitors users' activities within a service provider. Once a SAML token is issued, the user is funneled through Safous ZTA's App Gateway where it track users' actions within the service provider. The App Gateway translates the SAML request into a SAML service provider single sign-on (SAML SP SSO) which monitors users within the service provider.
Azure AD is provided here as an example. Any SAML-supporting IDP may be used following the same flow:
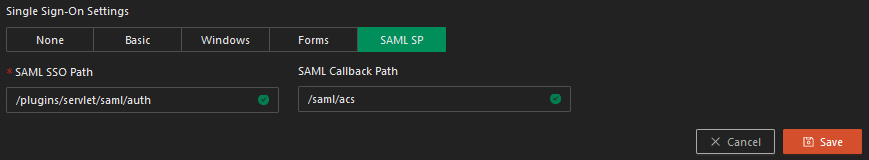
Configure SAML SSO Path in the Application
Step 1: Go to the Applications screen in the Admin Portal (portal.safous.com), there is a SAML SP button with a field labeled “SAML SSO Path.” This is the path that initiates the SAML request. The screen looks like this:
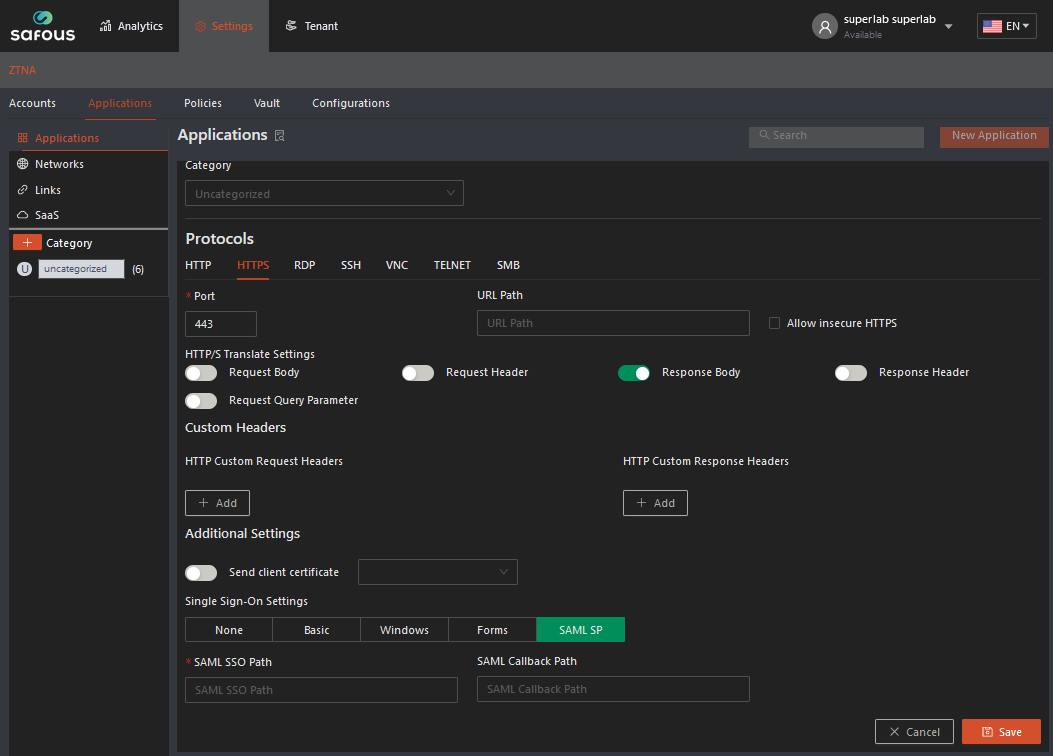
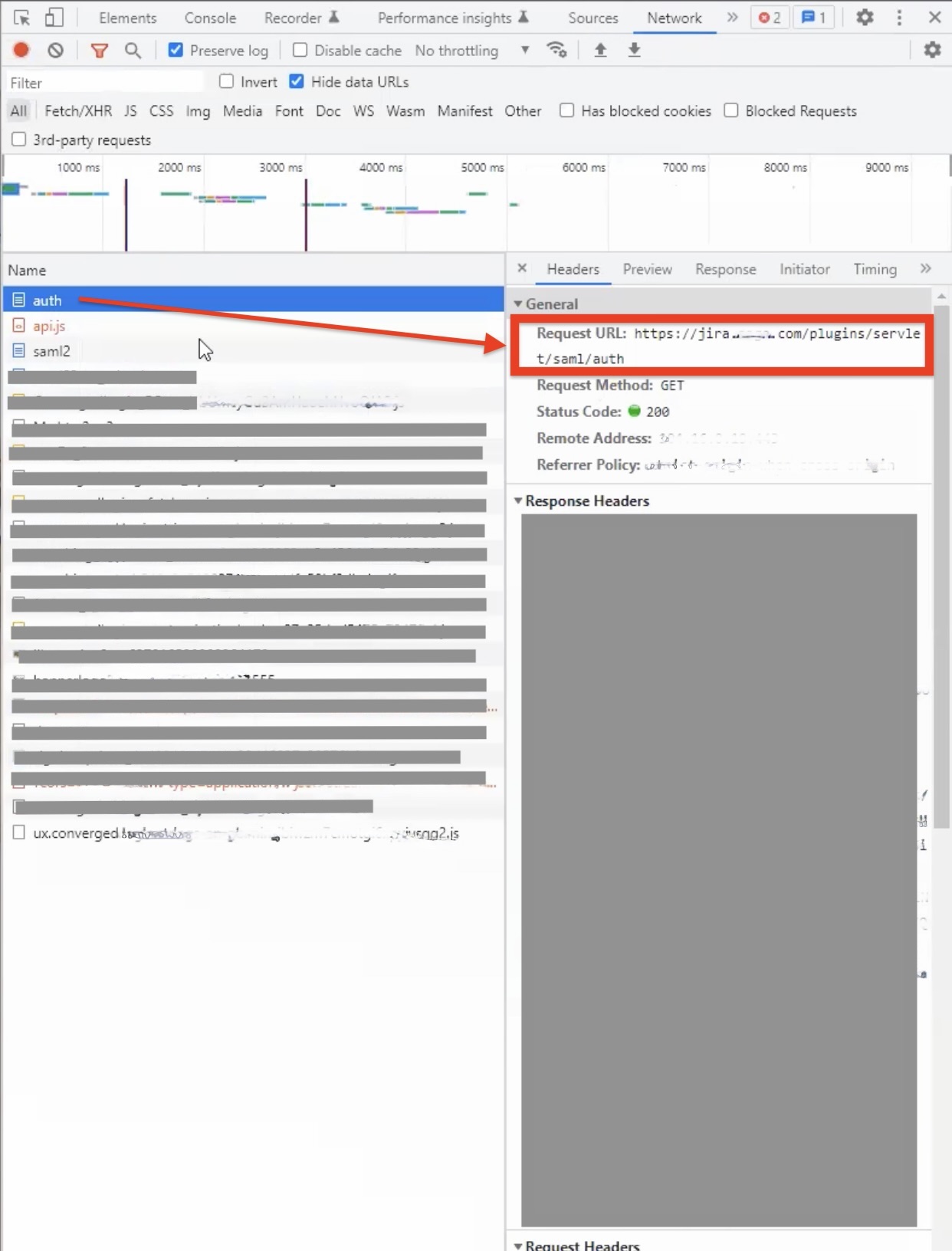
Step 2: The Administrator now needs to capture the link to the Service Provider page (for instance, in the screenshot below, it is Jira) that generated the SAML request and paste it into the Safous ZTA platform field as noted above. To find that link, go to the developer tools, accessed from the Chrome Browser (or any other network analysis tool), and to the network tab on the application page (see screenshot below). The link that generated the SAML request will be listed as the one that immediately precedes the SAML request. In the screenshot below, the red box on the right shows you the request URL:
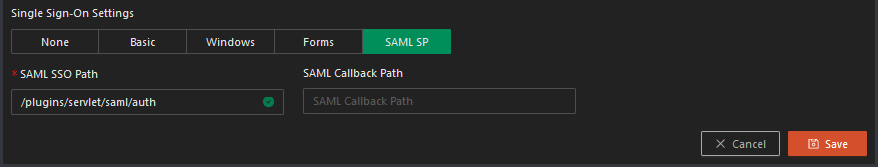
Step 3: Copy the request URL and paste it into the SAML SSO Path in the Safous ZTA Application page as shown in the screenshot below:
Step 4: Every IDP has closed lists of URLs. While they might slightly differ from one another, all of them have this list published, known as multiple assertion consumer service (ACS) URLs. In your IDP, you will need to enter two URLs into the ACS. Go to your IDP, look for the SAML application, and edit the basic SAML configuration to add the two additional URLs:
-
The application’s SAML SSO URL is entered on the Application page (this URL is likely already present, as shown in the screen below; you will probably only need to add the link in #2).
-
The return URL of the Safous ZTA application (e.g., https://jira.<TENANT>.ztna.safous.com/plugins/servlet/saml/auth).
Please make sure that both URLs are listed or the IDP won't respond. In our example, it looks like the screenshot below:
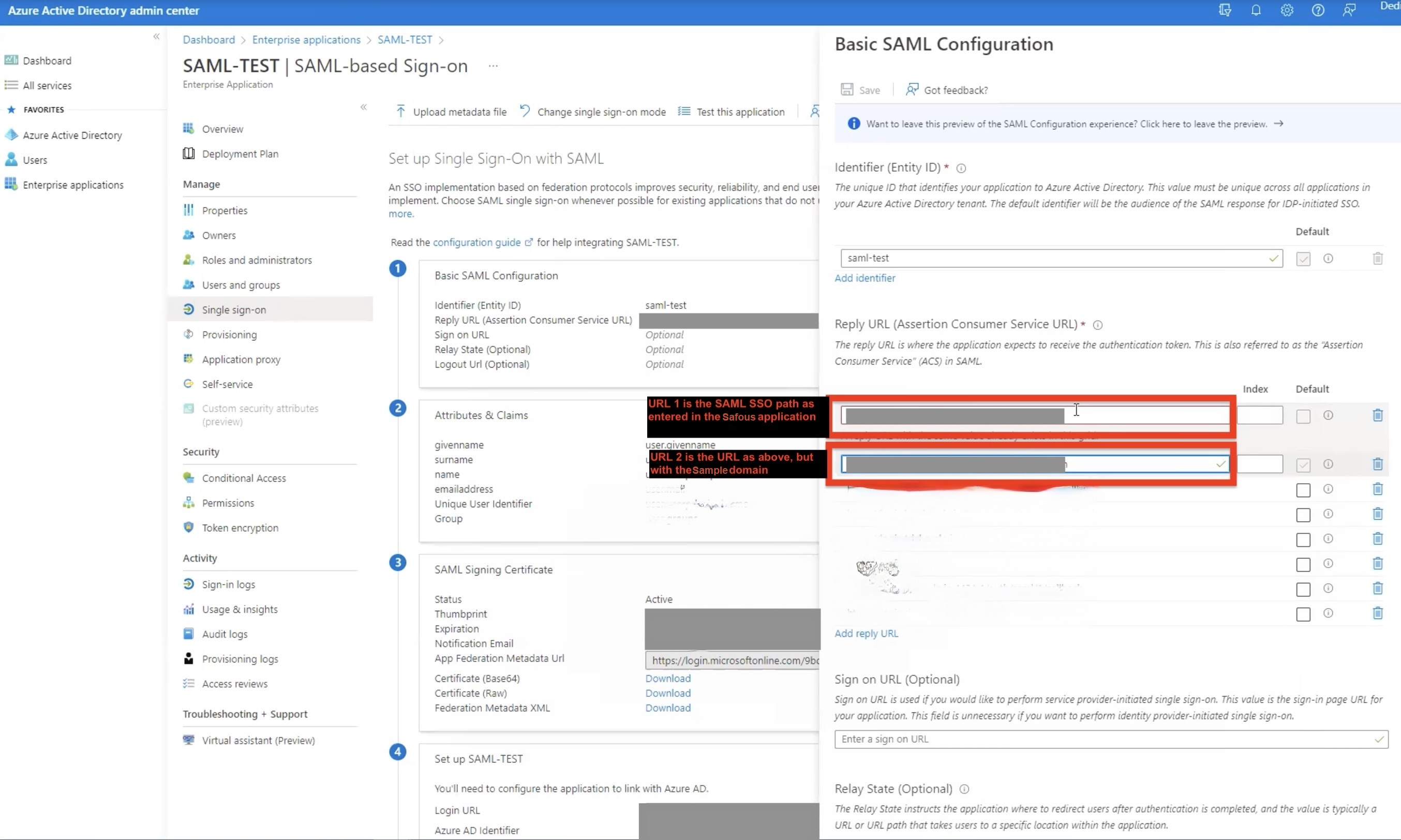
With this configuration, the IDP authorizes the address of the application that is published via Safous ZTA.
Configure the Callback Path
Azure AD is provided here as an example. Any SAML-supporting IDP may be used following the same flow.
Step 1: Capture the SAML/ACS link part from the reply URL in the IDP and paste it into the Safous ZTA platform field. To find that link, go to the developer tools, accessed from the Chrome Browser (or any other network analysis tool), and to the network tab in the application page (see screenshot below) Copy the link from the Reply URL (Assertion Consumer Service URL) as noted below:
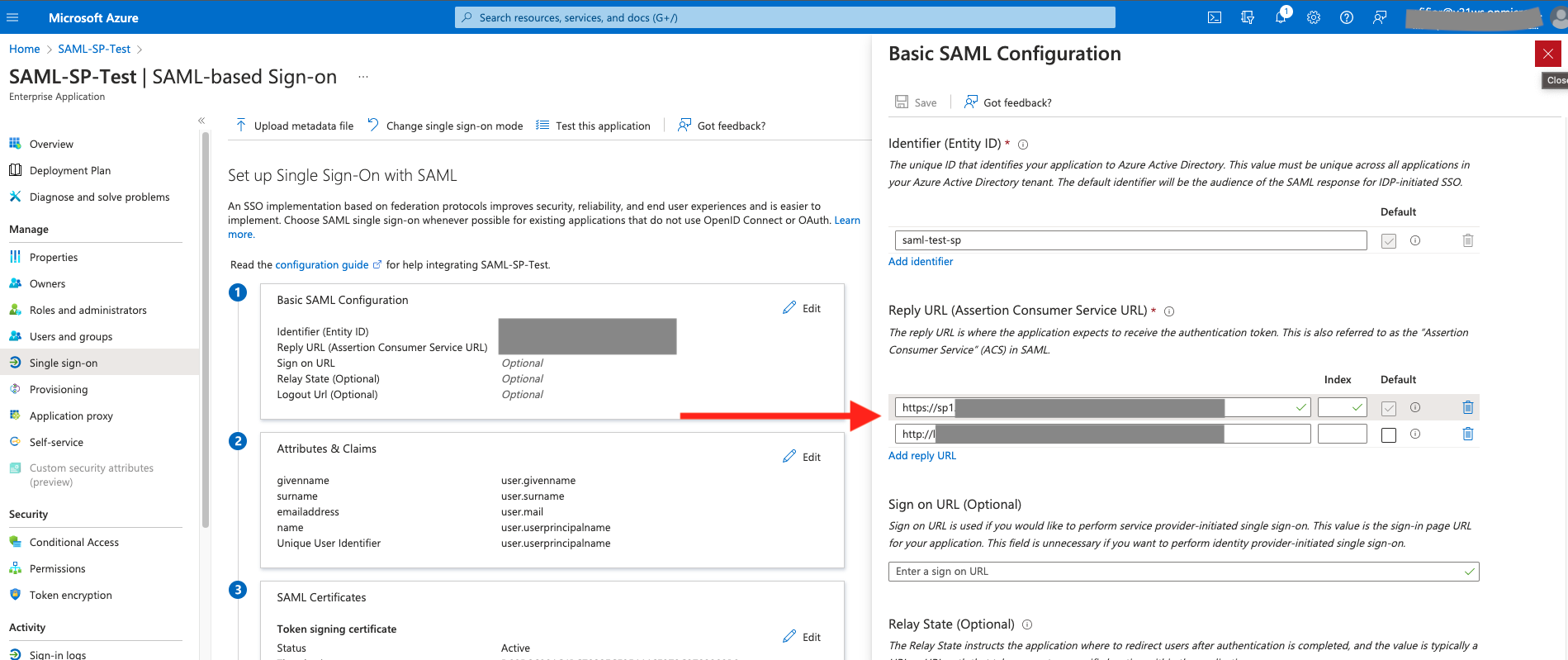
Step 2: Go to the Applications screen in the Admin Portal. In the Application screen, locate the SAML SP button and the field labeled “SAML Callback PathPath.” Paste the link (only the suffix) from Step 1 above into the Callback Path as shown in the screenshot below: