[ZTA] SSO to Github Enterprise
The article outlines the necessary steps to configure Safous as an Identity Provider (IdP) to facilitate Single Sign-On (SSO) with Github Enterprise serving as the Service Provider (SP).
Prerequisites
- Your organization is using Github Enterprise Plan.
- You have access to the GitHub Enterprise administrator account.
Register Github Enterprise as a SaaS Application on Safous Admin Portal
Please follow the steps outlined below to register Github Enterprise as a SaaS application on the Admin portal.
- Go to Settings > ZTNA > Applications > SaaS, then click the New SaaS button.
- Enter the name for the SaaS application. In this example, the name is simply github.
- Choose the site.
- Enter https://github.com/enterprises/<Enterpise>/saml/consume as the ACS URL. Replace <Enterprise> with the name of your Enterprise on Github.
- Enter https://github.com/enterprises/<Enterprise> as the Entity ID. Replace <Enterprise> with the name of your Enterprise on Github.
- Enter https://github.com/enterprises/<Enterpise>/saml/consume as the Relay State. Replace <Enterprise> with the name of your Enterprise on Github.
- Enable the Allow IDP-Initiated Flow toggle.
- Configure the Categories and Policies to associate to the application.
- Click Save.
- Your newly created SaaS application should resemble the image below. Please copy or take note of the generated SSO URL, Issuer and Certificate.
-png-1.png?width=688&height=412&name=image%20(2)-png-1.png)
Configure Safous as an IdP on Github Enterprise
This time we will register Safous as the IdP to use for SAML authentication on Github Enterprise in order to enable SSO.
- Open your Github Enterprise page (https://github.com/enterprises/<Enterprise>). Replace the <Enterprise> with the name of your Enterprise on Github.
- Navigate to Settings > Authentication Security. Click Require SAML authentication.
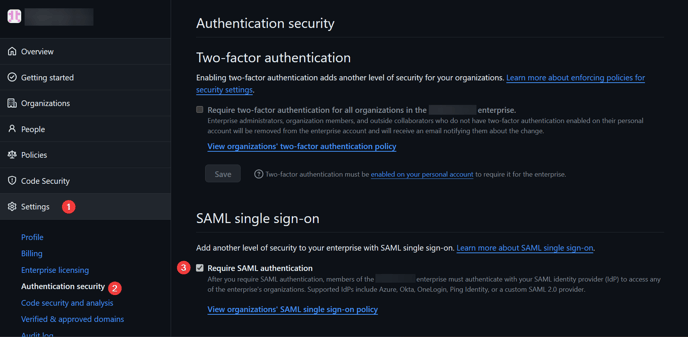
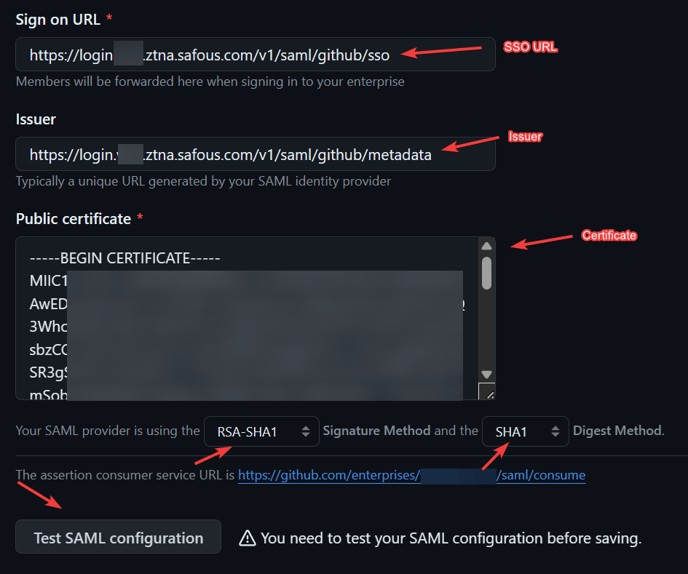
- Configure the IdP information as detailed below:
- Set Sign on URL with the previously copied value of SSO URL
- Set Issuer with the previously copied value of Issuer
- Set Public Certificate with the previously copied value of Certificate, and format it by wrapping the certificate like this:
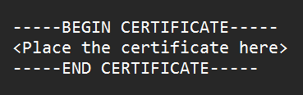
- Change the signature method to RSA-SHA1 and the digest method to SHA1
- Click on the Test SAML configuration button. This will initiate an SP-initiated SSO flow.
- You will be redirected to your Safous tenant's user portal. Log in to Safous user portal with a matching email to the user that exists in your Github Enterprise organization.
- After you have succesfully authenticated through Safous, you will be redirected back to the Github Enterprise settings page. Notice that the SSO test is successfully done.
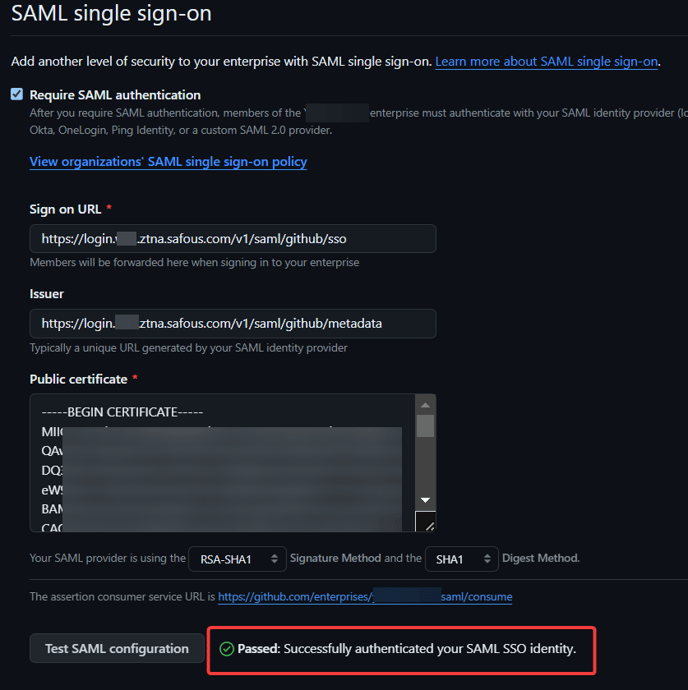
- Click Save SAML settings.
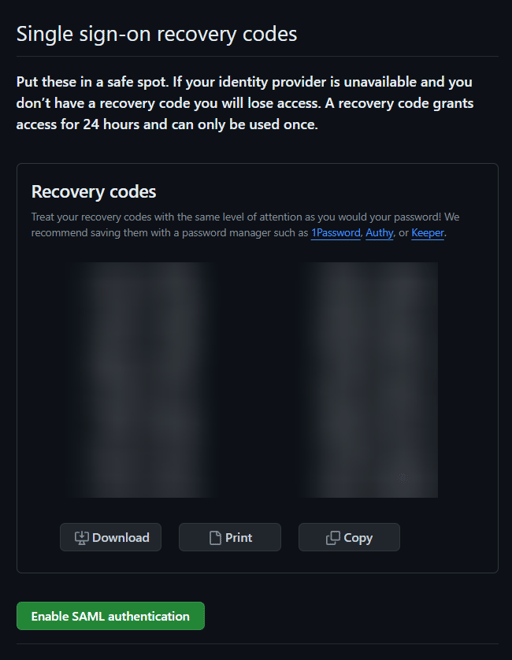
- Save the Single sign-on code generated by Github in a safe way then click Enable SAML Authentication.
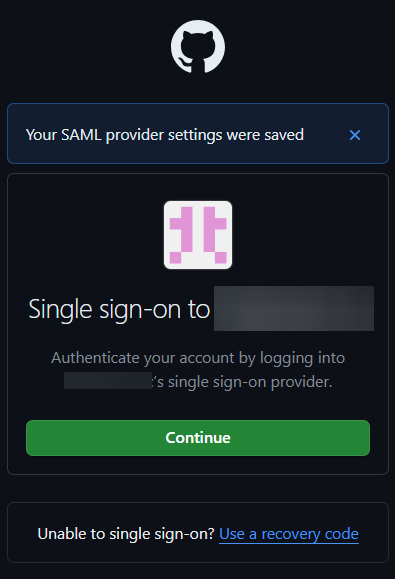
- As the SSO with SAML has been saved and applied, you will be prompted to log in to Github Enterprise page. Click Continue.
- As you have previously logged in to Safous user portal during the test, you will not be asked to reauthenticate again and can continue to the Github Enterprise page. Notice that the SAML SSO configuration for your Enterprise has been configured succesfully.
-png-1.png?width=688&height=300&name=image%20(6)-png-1.png)
Testing IdP-initiated SSO flow
As the SP-initiated SSO flow has been tested to be successfully working when we configured the SAML setting on Github Enterprise, we will now continue to test SSO with IdP-initiated flow.
- Go to your Safous tenant's user portal and log in with your credential.
- Click on the github SaaS application.
-png.png?width=688&height=282&name=image%20(7)-png.png)
- You are authenticated to access Github Enterprise resource.
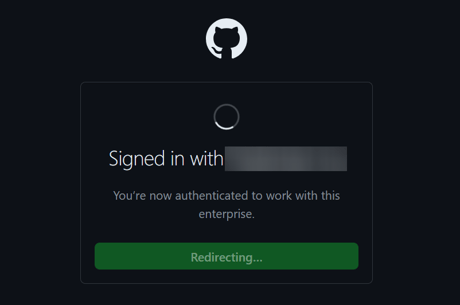
- Enter your Github personal account password to complete SSO.
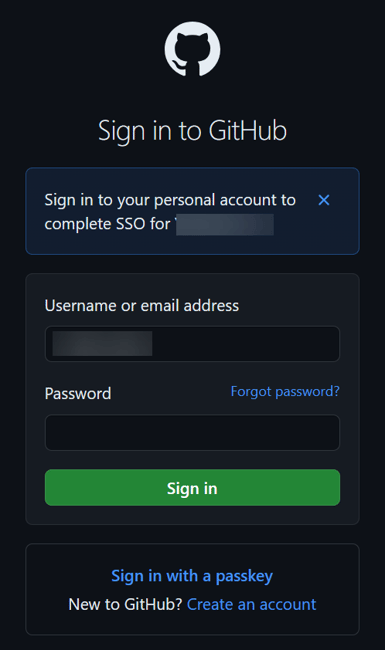
- Now you can access Github Enterprise page

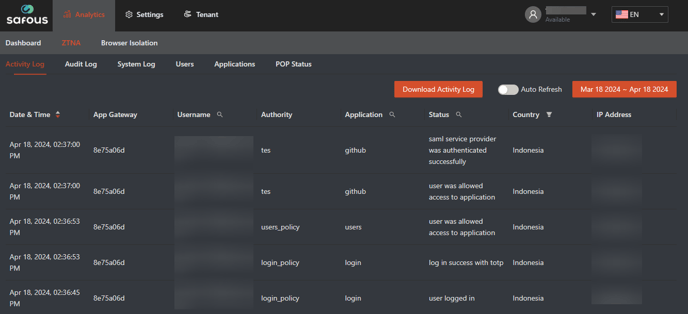
Logs
You can check the logs for SAML authentication on Safous admin portal.
- On Safous admin portal, go to Analytics > ZTNA > Activity Log