How to Enable Authentication to Salesforce using Safous App Gateway
This article covers the steps needed to configure SAML SSO for Salesforce in order to enable authentication via App Gateway along with the example images.
Prerequisites
- You have a Salesforce account with sufficient permissions to edit the configurations.
- You have access to Safous Admin Portal
- You have a running App Gateway
Configure App Gateway as Identity Provider (IdP)
- Log in to Salesforce as the user with sufficient permissions

- Go to Setup page

- Go to 'My Domain'

-
Copy the 'Current My Domain URL'

-
Go to Safous tenant admin portal and Create SaaS application with the https://<copied URL> as the value to fill in the required fields, i.e into ACS URL, Entity ID, Relay State field.
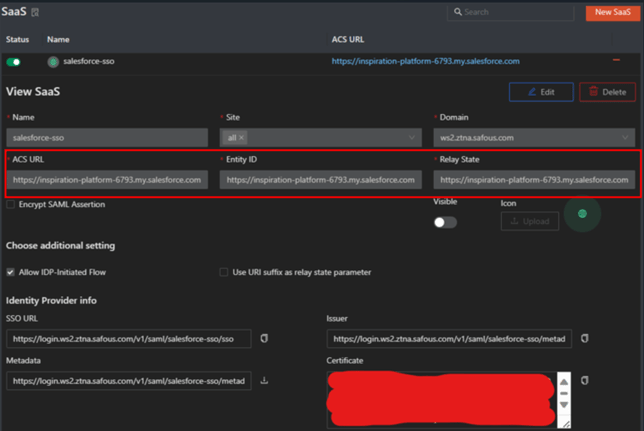
-
Create HTTPS application. Paste copied URL (Current My Domain URL) into the "Application Address/FQDN/Hostname" field.
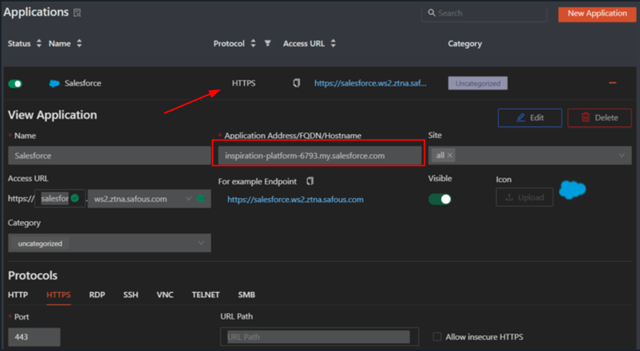
Also enable "Response Body" and "Request Query Parameter" on HTTP/S Translate Settings.png?width=688&height=239&name=image%20(2).png)
-
Map the created SaaS application and HTTPS application to a policy to enable users access
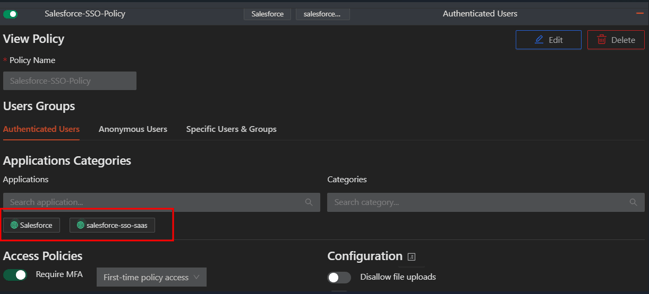
Configure Salesforce as Service Provider (SP)
This configuration assumes that you want App Gateway to be the only authentication method to log in to Salesforce. If you do not want that, you can enable the default Login Form from Salesforce on step 8. In that case, when you try to access the login page you will be presented with the default login option in addition with the option to log in via App Gateway at the bottom.
-
Go to SSO setting on the setup page

-
Click edit, check out the 'SAML Enabled' box then click save

-
Go to Safous tenant admin portal and download the metadata file from SaaS application

-
Make sure to change the file extension to .xml

-
Go back to the SSO setting page and Click 'New from Metadata file' button

-
Upload the metadata file and click create

-
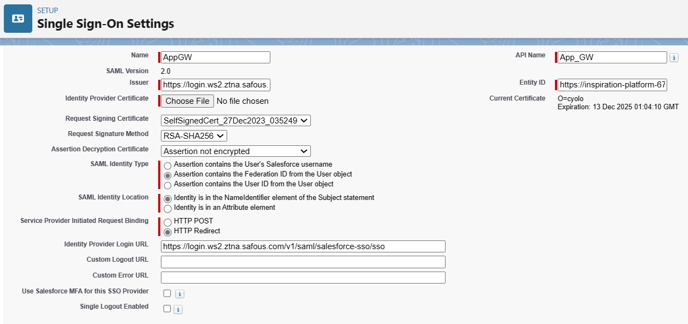
Verify all information match the correct values in the metadata file and resemble the configuration below. Please note that SAML Identity Type is set to "Assertion contains the Federation ID from the User object".
- Go to My Domain page and edit the authentication configuration to only allow authentication via App GW


-
Go to Users page and create users

-
Map Salesforce user and App GW user by filling out the value for Federation ID on Salesforce user with the username on App GW

Note:
If username on Salesforce is different with username on App GW (it's most cases), then the "federation ID" field, which is filled with username on App GW is required. Also the SAML Identity Type is set to "Assertion contains the Federation ID from the User object".
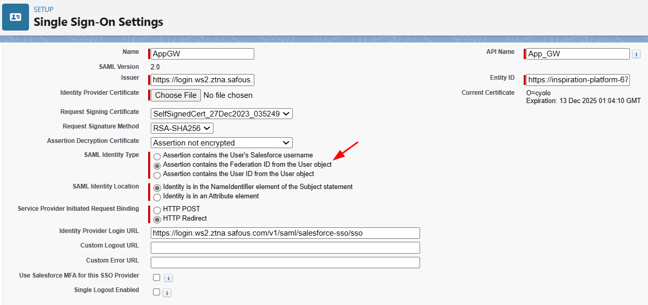
But if the username on Salesforce is exactly similar with username on App GW, then the federation ID is not required. Also the SAML Identity Type is set to "Assertion contains the User's Salesforce username".
Test User Access to Salesforce via App Gateway
-
Log in to Safous tenant user portal and click on the Salesforce app then you'll be granted access to the Salesforce

- Test result examples


-
Make sure to map the federation ID to the correct username in App GW as the name in Salesforce can be different from the username in App GW (App GW: Adam ➝ Salesforce: Alan)
-
If user try to access Salesforce through App GW without a matching Federation ID in Salesforce, they will get an error message.
-
When user try to directly access the login URL, they will be redirected to login via App GW (SP-initiated)