[PRA][ZTA] How to restrict access to Microsoft 365 with Safous
This procedure will guide you to configure Microsoft Entra and Safous to limit access to Microsoft Office365 Dashboard and services to be only accessible using Safous’ Application Gateway IP Address using Safous Agent.
🚧 Caution
Please be aware that this will limit users' access to M365 Services to be only accessible from specific IP addresses. Therefore, a static public IP address is needed for Application Gateway’s outbound access. A change in the IP address of outbound access will prevent users from accessing M365 services.
Please refer to the list of services that will be impacted after implementing this procedure—the link is at the bottom of this article.
Prerequisites
Before continuing the steps in this article, please ensure that your organization already have:
- Microsoft product licenses:
- At least Entra ID P1 license or Microsoft 365 Business Premium license to configure conditional access.
- Account in Microsoft Entra ID with these roles:
- Global Admin role to configure the settings mentioned in this article.
Create Conditional Access Policy in Entra ID
- Login to entra.microsoft.com and log in with the Global Administrator account
- Create Named Location
- Navigate to Protect and Secure -> Conditional Access -> Named locations -> and select add IP Ranges location

- Add the location name and list of IP addresses and mark it as a trusted location. If you have multiple App Gateways, add each of App Gateway's outbound IP Addresses here.
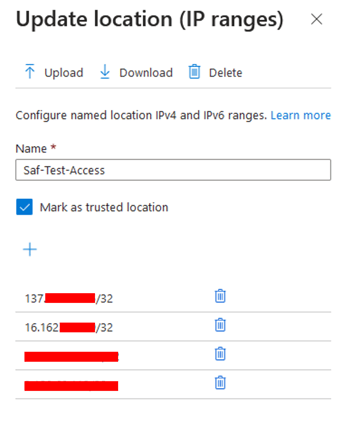
- To Check Safous Application Gateway public IP address, connect via SSH to the application gateway and run the below command,
(or you can use other IP address tracking service that supports curl such as ipconfig.io, ifconfig.me, etc.)curl ipconfig.io 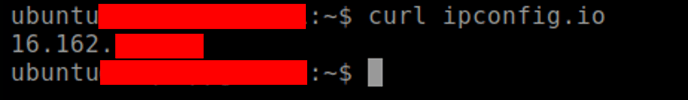
- Navigate to Protect and Secure -> Conditional Access -> Named locations -> and select add IP Ranges location
- Create a new conditional access policy
-
- Fill policy name and select the target users.
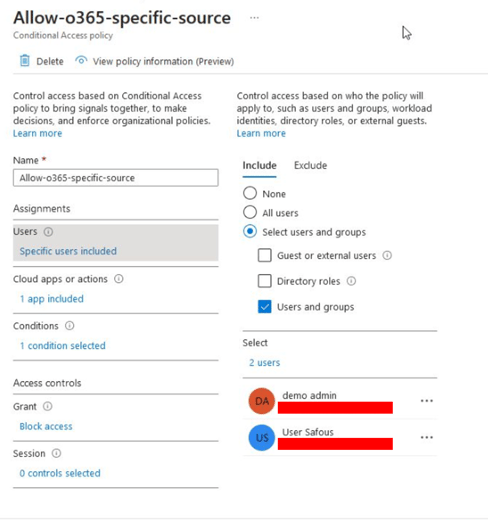
- Select the app that will be restricted. In this case, select Office365.
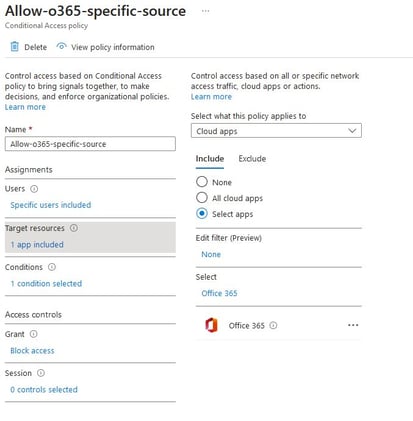
- Configure access condition and select location as the condition.
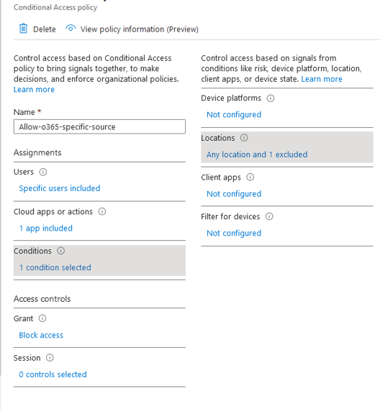
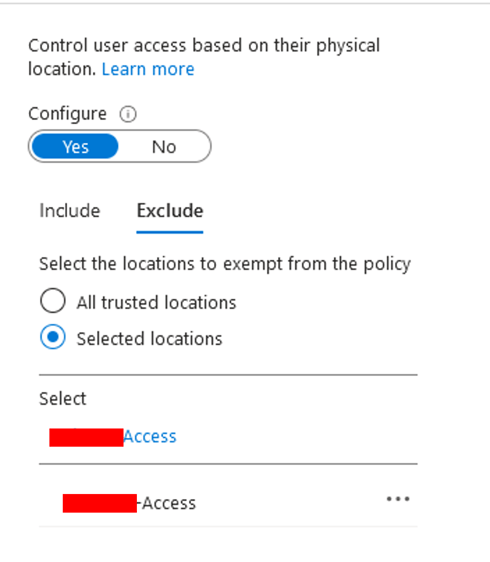
- Add the exclusion of a location in Configure section. Add the previously created trusted location.
- On the Grant section, select Block. This will block all access to Office365 Service except the trusted location that has been added to the exclusion list.
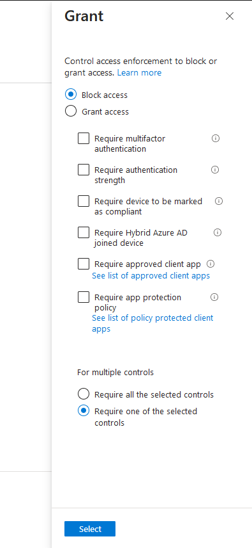
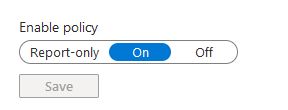
- Set Enable Policy to On to enforce this policy. If you want to apply this policy without enforcing it, select Report-only.
- Fill policy name and select the target users.
Testing Access
- Configure Safous Full Tunnel Network Application as mentioned in this article.
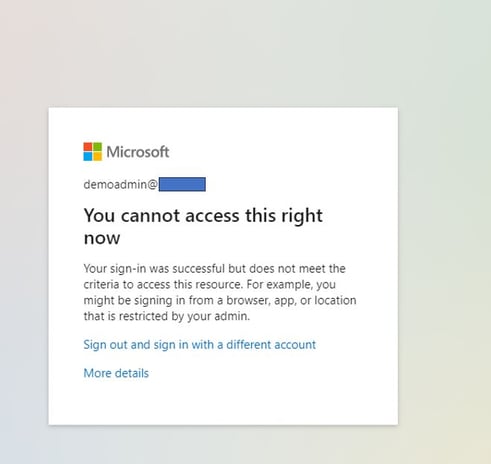
- Try login to Office365. Accessing from untrusted locations (without Safous Agent) will show the below output.
- Access should go through once device is connected to Full Tunnel Network Application
Please refer to the below link for documentation on the list of Office365 services that will be restricted: