WAF (Web Application Firewall) Configuration
Background:
The purpose of a web-application firewall (WAF) is to monitor, block and filter HTTP traffic into a web-application based on a predefined ruleset. The most basic ruleset defines filtering based on patterns in HTTP header and body in order to ensure that web-application security is not compromised when an oversized or malformed HTTP request arrives.
Adoption of OWASP Top Ten Protection:
The OWASP Top 10 is a standard awareness document that represents a broad consensus about the most critical security risks to web applications. The most recent OWASP Top Ten list was published in 2021 categorizing and listing the 10 most critical web application security risks. Safous ZTA platform adopted OWASP’s most recent top ten protections as noted here, and the feature is configurable in the Policy screen as noted below (WAF option only available once the web-application is put into the Applications field).
Configuring WAF:
Step 1: Navigate to the Admin Portal.
Step 2: Assuming web applications (HTTP/S) were already created, go to Settings > ZTNA > Policies and then create a New Policy or edit the existing one.
Step 3: As shown in the screenshot below:
-
Define users by selecting from the available options (e.g., Any authenticated user, Anonymous user, or Specific Identities)
-
Define applications by selecting the HTTP/S application previously created.
-
After configuring the Access tab, navigate to the Parameter tab. Go to the Web application firewall (WAF) which is disabled by default. To enable, toggle the feature on:
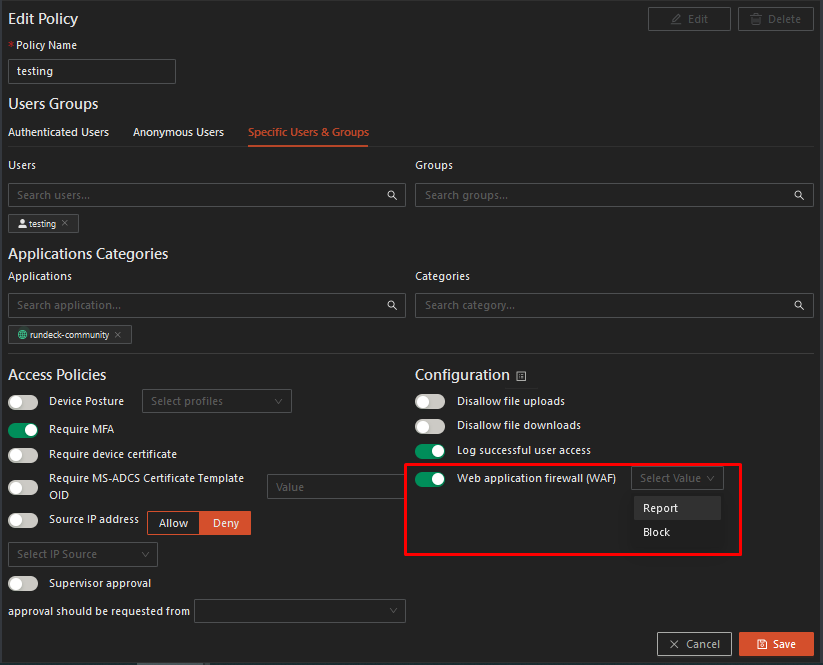
Step 4: When togging the WAF feature on, select from the two choices:
-
Report, which logs the WAF violation, in accordance with the OWASP top 10 rules, but does not block access for the specific request; or
-
Block, which blocks access to the specific request based on the OWASP top 10 rules, and logs the block.